var q yzshadowforwindows7Windows 7 Home and Ultimate editions have been retired. If you want to get a computer without Windows 8. 1, your options are limited. We have compiled them for you. Windows is swimming in a sea of free applications. Which ones can you trust and which ones are the best If youre unsure or need to solve a specific task, consult. Xian Y 7 Wikipedia. The Xian Y 7 Chinese 7 pinyin Yn q is a transport aircraft built in the Peoples Republic of China. 1 It is based on the Soviet designed Antonov An 2. Worried if your favorite game is supported by Windows 10 Heres the list of all Windows 10 compatible games and the unsupported ones too. Black Friday special Save 20 on the entire collection of creative apps, including Photoshop, Illustrator, Premiere Pro, and more. It seems like the shortcuts Ive been using for years in previous versions of Word are not working anymore. For example CtrlZ, CtrlC, CtrlV are not working there. Windows 7 Services The last time I did a services related article was right after the release of Service Pack 1 for Windows XP. I skipped over Vista completely.  Whats Hot Your spot for viewing some of the best pieces on DeviantArt. Be inspired by a huge range of artwork from artists around the world. Hello,I have been having random freezeshangs in windows 7 with no BSOD. I left it on for about 30mins to see if anything happens eventually and still no BSOD. Its. Latest trending topics being covered on ZDNet including Reviews, Tech Industry, Security, Hardware, Apple, and Windows.
Whats Hot Your spot for viewing some of the best pieces on DeviantArt. Be inspired by a huge range of artwork from artists around the world. Hello,I have been having random freezeshangs in windows 7 with no BSOD. I left it on for about 30mins to see if anything happens eventually and still no BSOD. Its. Latest trending topics being covered on ZDNet including Reviews, Tech Industry, Security, Hardware, Apple, and Windows.  DevelopmenteditThe Peoples Republic of China imported the Antonov An 2. In 1. 96. 6, Xian aircraft factory started the project of local production of An 2. The first Chinese assembled An 2. T had its maiden flight on 2. December 1. 97. 0. Production was launched in 1. Xian aircraft factory but progress was slow due to the deleterious effects of the Cultural Revolution, with a pre production aircraft displayed to the public at Nanyuan air base, near Beijing, on 1. April 1. 98. 2. The WJ 5. A1 turboprop engine was chosen as the Y 7s power source. The first production aircraft was not flown until February 1. The Chinese aircraft equated to the An 2. RV, having a full complement of windows and the booster jet engine. The majority of early deliveries were to the Peoples Liberation Army Air Force PLAAF, mostly as transports, with a few in 5. Civil Aviation Administration of China CAAC. After the initial licensed production run the Y 7 was developed separately from the An 2. Xian MA6. 0 Modern Ark series. 2A tactical transport derivative was copied, unlicensed, from the Antonov An 2. Y 7. H, incorporating the cargo ramp door and military equipment of the An 2. VariantseditXian Y 7. ESpeculative designation for a Hot and High version with more powerful engines. 1Xian Y 7. GA military variant of the MA6. PLAAF. 1Xian Y 7. HHao cargo A reverse engineered An 2. PLAAF, entering production in 1. Xian Y7. H 5. 00. Civil variant of the Y 7. H certified in 1. Xian Y 1. 4The original designation for the An 2. Y 7. H. 1Xian Y 7 1. Improved version, developed in co operation with HAECO Hong Kong Aircraft Engineering Company, with redesigned cockpit and cabin, as well as winglets. 1 This variation was added upgraded passenger cabin interior, new avionics sourced from western providers. Flight crew was down to three, it is capable of carrying 5. Xian Y 7 1. 00. C1. Five crew variant with equipment changes. Xian Y 7 1. 00. C2. Five crew variant with equipment changes. Xian Y 7 1. 00. C3. Five crew variant with equipment changes. Xian Y 7 2. 00. Fitted with new avionics without winglets. 1Xian Y 7 2. APowered by two Pratt Whitney PW1. C turboprop engines. 1Xian Y 7 2. BStretched version 7. WJ5. A 1. G engines, built for the Chinese domestic market. 1Xian HYJ 7Hongzhaji Yunshuji Jiaolianji Bombertransporttrainer A pilot and crew trainer for H 6 heavy bombers fitted with a stabilised HM 1. A bombsight, bomb aiming radar and a TNL 7. Xian MA6. 0Y 7 MA6. Modern Ark 6. 0 seats A westernised variant of the Y 7 intended to attract more western customers and meet Joint Airworthiness Requirements. 1Xian JZY 0. Y 7 AWACSCarrier based AWACS variant. JZY stands for Jian Zai Yu, meaning carrier borne AEW, has 4 rudders like E 2 AEW34OperatorseditCurrent operators Peoples Republic of China. Former operators Cambodia Iran Laos Mauritania Peoples Republic of China Zimbabwe. Accidents and incidentseditOn 2. June 2. 00. 0, Wuhan Airlines Flight 3. Sitai, Yongfeng, killing all 4. This crash is the worst ever accident involving the Y 7. On 1. 9 October 2. Peoples Liberation Army Air Force Y 7 crashed into a wheat field near Hengshui, killing two. Specifications Y7 1. Data from1General characteristics. Crew 3. Payload 5,5. Length 2. 4. 2. 18m 7. Wingspan 2. 9. 6. Height 8. 5. 53m 2. Wing area 7. 5. 2. Airfoil Ts. AGI S 52Empty weight 1. Max. takeoff weight 2. Powerplant Performance. Maximum speed 5. Cruise speed 6,0. Range max payload 9. Service ceiling 8,7. Take off run at max. TOW 6. 40m2,1. 00ftReferenceseditNotes. Bibliography. External linksedit. Keyboard shortcuts such as Ctrl C, Ctrl V and Ctrl Z not working in Word 2. Windows 7. I hadhave the same issue. It is not clear why this happens, couldnt find any Microsoft blog post or something that confirms this, BUT, when looking through the Word 2. I have found that there was a complete revamp of the shortcuts. To restore word to the way you remember, you need to go to, File Options Customize Ribbon. On the bottom there is a label Keyboard Shortcuts and a button Customize. click it. On the Categories box, scroll until you find All Commands and select it. Now, from the right box select the following Command Edit. Copy. Look at the Current Keys Box you will see CtrlInsert which is the NEW mapping. Press new shortcut key and Press CtrlC, a button on the bottom named Assign will light up, and you click on it. Do the same for all the shortcuts you like, such as Edit. Paste, Edit. Undo, Edit. Redo, Edit. Cut, Select. All etc, then save. Now everything works perfectly. Again, Im not clear why this wasnt communicated by MS, it seems they are trying to force a new old standard on us that was used in mac for a long time.
DevelopmenteditThe Peoples Republic of China imported the Antonov An 2. In 1. 96. 6, Xian aircraft factory started the project of local production of An 2. The first Chinese assembled An 2. T had its maiden flight on 2. December 1. 97. 0. Production was launched in 1. Xian aircraft factory but progress was slow due to the deleterious effects of the Cultural Revolution, with a pre production aircraft displayed to the public at Nanyuan air base, near Beijing, on 1. April 1. 98. 2. The WJ 5. A1 turboprop engine was chosen as the Y 7s power source. The first production aircraft was not flown until February 1. The Chinese aircraft equated to the An 2. RV, having a full complement of windows and the booster jet engine. The majority of early deliveries were to the Peoples Liberation Army Air Force PLAAF, mostly as transports, with a few in 5. Civil Aviation Administration of China CAAC. After the initial licensed production run the Y 7 was developed separately from the An 2. Xian MA6. 0 Modern Ark series. 2A tactical transport derivative was copied, unlicensed, from the Antonov An 2. Y 7. H, incorporating the cargo ramp door and military equipment of the An 2. VariantseditXian Y 7. ESpeculative designation for a Hot and High version with more powerful engines. 1Xian Y 7. GA military variant of the MA6. PLAAF. 1Xian Y 7. HHao cargo A reverse engineered An 2. PLAAF, entering production in 1. Xian Y7. H 5. 00. Civil variant of the Y 7. H certified in 1. Xian Y 1. 4The original designation for the An 2. Y 7. H. 1Xian Y 7 1. Improved version, developed in co operation with HAECO Hong Kong Aircraft Engineering Company, with redesigned cockpit and cabin, as well as winglets. 1 This variation was added upgraded passenger cabin interior, new avionics sourced from western providers. Flight crew was down to three, it is capable of carrying 5. Xian Y 7 1. 00. C1. Five crew variant with equipment changes. Xian Y 7 1. 00. C2. Five crew variant with equipment changes. Xian Y 7 1. 00. C3. Five crew variant with equipment changes. Xian Y 7 2. 00. Fitted with new avionics without winglets. 1Xian Y 7 2. APowered by two Pratt Whitney PW1. C turboprop engines. 1Xian Y 7 2. BStretched version 7. WJ5. A 1. G engines, built for the Chinese domestic market. 1Xian HYJ 7Hongzhaji Yunshuji Jiaolianji Bombertransporttrainer A pilot and crew trainer for H 6 heavy bombers fitted with a stabilised HM 1. A bombsight, bomb aiming radar and a TNL 7. Xian MA6. 0Y 7 MA6. Modern Ark 6. 0 seats A westernised variant of the Y 7 intended to attract more western customers and meet Joint Airworthiness Requirements. 1Xian JZY 0. Y 7 AWACSCarrier based AWACS variant. JZY stands for Jian Zai Yu, meaning carrier borne AEW, has 4 rudders like E 2 AEW34OperatorseditCurrent operators Peoples Republic of China. Former operators Cambodia Iran Laos Mauritania Peoples Republic of China Zimbabwe. Accidents and incidentseditOn 2. June 2. 00. 0, Wuhan Airlines Flight 3. Sitai, Yongfeng, killing all 4. This crash is the worst ever accident involving the Y 7. On 1. 9 October 2. Peoples Liberation Army Air Force Y 7 crashed into a wheat field near Hengshui, killing two. Specifications Y7 1. Data from1General characteristics. Crew 3. Payload 5,5. Length 2. 4. 2. 18m 7. Wingspan 2. 9. 6. Height 8. 5. 53m 2. Wing area 7. 5. 2. Airfoil Ts. AGI S 52Empty weight 1. Max. takeoff weight 2. Powerplant Performance. Maximum speed 5. Cruise speed 6,0. Range max payload 9. Service ceiling 8,7. Take off run at max. TOW 6. 40m2,1. 00ftReferenceseditNotes. Bibliography. External linksedit. Keyboard shortcuts such as Ctrl C, Ctrl V and Ctrl Z not working in Word 2. Windows 7. I hadhave the same issue. It is not clear why this happens, couldnt find any Microsoft blog post or something that confirms this, BUT, when looking through the Word 2. I have found that there was a complete revamp of the shortcuts. To restore word to the way you remember, you need to go to, File Options Customize Ribbon. On the bottom there is a label Keyboard Shortcuts and a button Customize. click it. On the Categories box, scroll until you find All Commands and select it. Now, from the right box select the following Command Edit. Copy. Look at the Current Keys Box you will see CtrlInsert which is the NEW mapping. Press new shortcut key and Press CtrlC, a button on the bottom named Assign will light up, and you click on it. Do the same for all the shortcuts you like, such as Edit. Paste, Edit. Undo, Edit. Redo, Edit. Cut, Select. All etc, then save. Now everything works perfectly. Again, Im not clear why this wasnt communicated by MS, it seems they are trying to force a new old standard on us that was used in mac for a long time.

 Machinery Exchange. A worldwide buyer and seller exchange for woodworking machinery and equipment. Dcouvrez le Guide de leau. Le Guide de lEau est un guide technique et professionnel, spcialis dans le domaine de leau et de lenvironnement. HOLZ EDV Alles rund um den PC Branchenprogramm, CNC, CAD etc. Classified Ad Exchange. Classified advertising for the woodworking industry for advertisements that do not include machinery, lumber products and employment listings. Adhesives Forum. Discussing topics related to adhesives within the woodworking industry. Architectural Woodworking Forum. Discussing quality standards and production of architectural wood products. Business and Management Forum. A forum for the discussion of business topics from sales and marketing to dealing with difficult customers. Cabinet and Millwork Installation Forum. Discussing all aspects of installation issues encountered by cabinet and millwork installers. Cabinetmaking Forum. Discussing 3. 2mm and face frame cabinet construction including fabrication, casegoods design, and installation.
Machinery Exchange. A worldwide buyer and seller exchange for woodworking machinery and equipment. Dcouvrez le Guide de leau. Le Guide de lEau est un guide technique et professionnel, spcialis dans le domaine de leau et de lenvironnement. HOLZ EDV Alles rund um den PC Branchenprogramm, CNC, CAD etc. Classified Ad Exchange. Classified advertising for the woodworking industry for advertisements that do not include machinery, lumber products and employment listings. Adhesives Forum. Discussing topics related to adhesives within the woodworking industry. Architectural Woodworking Forum. Discussing quality standards and production of architectural wood products. Business and Management Forum. A forum for the discussion of business topics from sales and marketing to dealing with difficult customers. Cabinet and Millwork Installation Forum. Discussing all aspects of installation issues encountered by cabinet and millwork installers. Cabinetmaking Forum. Discussing 3. 2mm and face frame cabinet construction including fabrication, casegoods design, and installation.  CAD Forum. Shedding light on the all too often shadowy world of CAD. CNC Forum. Discussing CNC computer numerically controlled woodworking equipment, software, and automated product manufacturing. Dust Collection, Safety and Plant Operation Forum. Discussing topics related to maintaining a safe and productive working environment. Professional Finishing Forum. Finishing issues for the production environment. Forestry Forum. The science and art of forest cultivation and timber management, planting, surveying, tree diseases, silviculture and timber harvesting. Professional Furniture Making Forum. Helping professional furniture makers improve quality, save time, and increase profits. Laminating and Solid Surfacing Forum. Issues related to laminating and solid surface materials and processes. Commercial Kiln Drying Forum. Discussions covering issues faced be commercial drying operations that process at least 7. Sawing and Drying Forum. Discussing topics related to primary processing and drying of lumber. Solid Wood Machining Forum. Discussing topics related to the machining of solid wood. Value Added Wood Products Forum. Learn how to improve your output, find new markets, and boost sales of your lumber products. Veneer Forum. Discussing topics related to veneer processing, manufacturing, and fabrication. WOODnet. WORKAn electronic discussion group for woodworkers throughout the world.
CAD Forum. Shedding light on the all too often shadowy world of CAD. CNC Forum. Discussing CNC computer numerically controlled woodworking equipment, software, and automated product manufacturing. Dust Collection, Safety and Plant Operation Forum. Discussing topics related to maintaining a safe and productive working environment. Professional Finishing Forum. Finishing issues for the production environment. Forestry Forum. The science and art of forest cultivation and timber management, planting, surveying, tree diseases, silviculture and timber harvesting. Professional Furniture Making Forum. Helping professional furniture makers improve quality, save time, and increase profits. Laminating and Solid Surfacing Forum. Issues related to laminating and solid surface materials and processes. Commercial Kiln Drying Forum. Discussions covering issues faced be commercial drying operations that process at least 7. Sawing and Drying Forum. Discussing topics related to primary processing and drying of lumber. Solid Wood Machining Forum. Discussing topics related to the machining of solid wood. Value Added Wood Products Forum. Learn how to improve your output, find new markets, and boost sales of your lumber products. Veneer Forum. Discussing topics related to veneer processing, manufacturing, and fabrication. WOODnet. WORKAn electronic discussion group for woodworkers throughout the world. 
 It employs a software engine that provides the geographical location of devices with an accuracy of 1. A map on the in. Sync dashboard makes i easy to see where enabled devices are located. Safe. Point provides an instant view of the location of remote endpoint devices as they come online, with details such as street, city, state, or country. It enables the initiation of a remote decommission to wipe critical data from the device and prevent data breach. This is an avenue you might want to explore if you want to prevent the headache you are about to experience with the unsecured data on your computer from recurring at some point in the future. Free trials are available here DELETED BY MODERATOROther sources DELETED BY MODERATOR. NOT AGAIN PLEASE.
It employs a software engine that provides the geographical location of devices with an accuracy of 1. A map on the in. Sync dashboard makes i easy to see where enabled devices are located. Safe. Point provides an instant view of the location of remote endpoint devices as they come online, with details such as street, city, state, or country. It enables the initiation of a remote decommission to wipe critical data from the device and prevent data breach. This is an avenue you might want to explore if you want to prevent the headache you are about to experience with the unsecured data on your computer from recurring at some point in the future. Free trials are available here DELETED BY MODERATOROther sources DELETED BY MODERATOR. NOT AGAIN PLEASE. 
 Mask My IP Pro Full Version Free Download With Patch Full and Free Internet Download Manager 6 Build 8 PatchSerial Download Winamp Pro 5. 63 Full. Typing master Pro latest v7. 0 full version Free download with serial key crack and keygen Shortcut keys to create a New Folder in Windows Seven Explorer Hot keys or. Antivirus or antivirus software often abbreviated as AV, sometimes known as antimalware software, is computer software used to prevent, detect and remove. It consists various modules that are useful elements for protection. These modules have a function that is particular, but as a whole, they are ready for managing different kinds of threats. AVG Internet Security 2. License Key the multiple features and modules are arranged in the Manu that is same, so you will never feel difficult without knowing what to do next. Additionally, it has attractive design look that is graphical. It has a capacity that is an excellent stop virus infections and another type of malware, AVG Internet Security 2. License Key ranks among the most effective anti virus software available. We will see the console, which acts as a major in operation for all the modules when we begin to AVG Internet Security 2. Feature Advantages of AVG Internet Security 2. License Key High speed scanning performance. Newly enhanced virus scanner.
Mask My IP Pro Full Version Free Download With Patch Full and Free Internet Download Manager 6 Build 8 PatchSerial Download Winamp Pro 5. 63 Full. Typing master Pro latest v7. 0 full version Free download with serial key crack and keygen Shortcut keys to create a New Folder in Windows Seven Explorer Hot keys or. Antivirus or antivirus software often abbreviated as AV, sometimes known as antimalware software, is computer software used to prevent, detect and remove. It consists various modules that are useful elements for protection. These modules have a function that is particular, but as a whole, they are ready for managing different kinds of threats. AVG Internet Security 2. License Key the multiple features and modules are arranged in the Manu that is same, so you will never feel difficult without knowing what to do next. Additionally, it has attractive design look that is graphical. It has a capacity that is an excellent stop virus infections and another type of malware, AVG Internet Security 2. License Key ranks among the most effective anti virus software available. We will see the console, which acts as a major in operation for all the modules when we begin to AVG Internet Security 2. Feature Advantages of AVG Internet Security 2. License Key High speed scanning performance. Newly enhanced virus scanner.  Easy to block viruses, spyware, malware and other software that is harmful. Fully protects you against dangerous downloads. Support password protection of private files. Effectively stops spammers and scammers. Effectively blocks hackers so you can buy securely. Surf Shield for each Web page you visit before opening. Download and exchange files without risk of infection.
Easy to block viruses, spyware, malware and other software that is harmful. Fully protects you against dangerous downloads. Support password protection of private files. Effectively stops spammers and scammers. Effectively blocks hackers so you can buy securely. Surf Shield for each Web page you visit before opening. Download and exchange files without risk of infection. 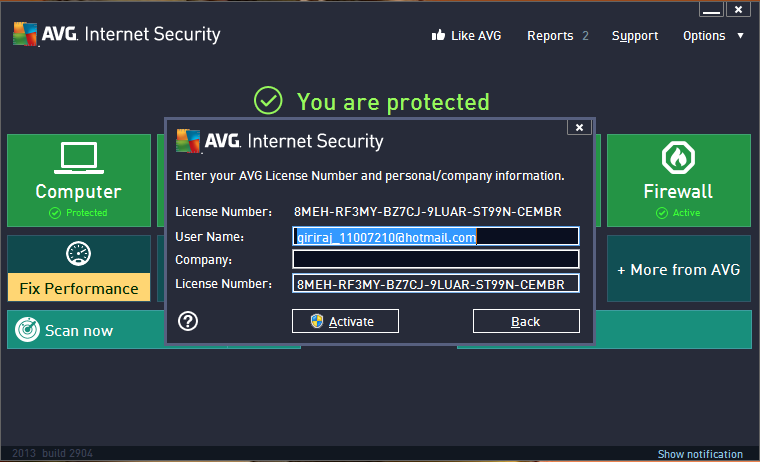
 Keep safe from dangerous attachments and links in your e mail. Update automatically to protect against the latest threats. Simple installation process. Well designed interface. ESET NOD32 Antivirus, commonly known as NOD32, is an antivirus software package made by the Slovak company ESET. ESET NOD32 Antivirus is sold in two editions, Home. Microsoft Office 2013 Free download full version Allows use Customize the ribbon and select their preferred language. Office 2013 Free download full version. Download FREE antivirus and malware protection. Tune up your PC, Mac and Android devices for peak performance. Surf safely and privately, wherever you are. Avast Free Antivirus is an efficient and comprehensive antivirus program. It is one of the most popular antivirus programs available, thanks to the reliable and. Deals with traffic monitoring and mail that is filtering. Efficient anti spam module for filtration of received messages. Got Website feature that is blocking. Each component of AVG Antivirus 2. License Key may warrant consideration that is separate. First, it is the component that is the antivirus. It works in real time to protect your computer at any time from a number that is mostly of and spyware. Also, you can start scans that are complete with folders or files. Moreover, you can schedule scans that are regular. Second, there is the Identity Protection feature, which completes the work of the component that is antivirus monitoring the actions of unknown pieces of code. The third is the email protection, which is a scanner that is powerful detects threats contained in email messages and filter spam. Fourth, Link Scanner prevents attacks from dangerous websites while browsing on the Internet. Fifth, the firewall component monitors all traffic that runs on network ports on your computer. Sixth, the kit that is anti Root detects rootkits and prevents them from taking control of your operating system. Finally, there is the PC Analyzer, a tool that scans your system for errors. AVG Internet Security 2. License Key Free. Version. The installation procedure is pretty straightforward, and in a few minutes, you will be able to get this protection app that is useful. You just need to restart your system so that the application becomes fully functional. AVG Internet Security 2. Crack has also been wholly equipped for traffic mail and monitoring filtering. AVG Internet Security 2. It has got blocking a Website feature also that can block all the websites that are annoying. Overall, AVG Internet Security 2. You feel that having too many options to take you should not worry because most of these features almost never need to be configured, but they will always be there for your protection if you are a beginner and. Even the virus database will automatically be updated. System Requirements for AVG Internet Security 2. License Key OS Windows 788. Memory RAM 1. GBHard Disk 1. 20. MBCPU Intel Pentium 4 or later. Here is License Keys 8. MEH RU7. JQ ACDRM MQEPR G3. S2. 3 FEMBR ACED8. MEH RW2. ZU 2. 9S4. F 2. 6QCR WT4. 82 BEMBR ACED8. MEH RNZLL 2. Y4. QX 7. 9PPA MMOKE AEMBR ACED8. MEH RREY3 L2. LQA LUMOR UDTZ4 6. EMBR ACED8. MEH RF3. MY BZ7. CJ 9. LUAR ST9. N CEMBR ACED8. MEH RMXLW HN4. A BABPA S9. NQF PEMBR ACED8. MEH RGM3. 3 K4. L 6. FGRR 8. RR7. K UEMBR ACEDHow to Download AVG Internet Security 2. License Key Just follow the instructions and start protecting your system. Click Here to download AVG Internet Security 2. License Key. Now disconnect the internet. Use AVG Internet Security AVG Internet Security 2. License Key for activation. Now use AVG Internet Security that is fully active 2. Malwarebytes Download is here.
Keep safe from dangerous attachments and links in your e mail. Update automatically to protect against the latest threats. Simple installation process. Well designed interface. ESET NOD32 Antivirus, commonly known as NOD32, is an antivirus software package made by the Slovak company ESET. ESET NOD32 Antivirus is sold in two editions, Home. Microsoft Office 2013 Free download full version Allows use Customize the ribbon and select their preferred language. Office 2013 Free download full version. Download FREE antivirus and malware protection. Tune up your PC, Mac and Android devices for peak performance. Surf safely and privately, wherever you are. Avast Free Antivirus is an efficient and comprehensive antivirus program. It is one of the most popular antivirus programs available, thanks to the reliable and. Deals with traffic monitoring and mail that is filtering. Efficient anti spam module for filtration of received messages. Got Website feature that is blocking. Each component of AVG Antivirus 2. License Key may warrant consideration that is separate. First, it is the component that is the antivirus. It works in real time to protect your computer at any time from a number that is mostly of and spyware. Also, you can start scans that are complete with folders or files. Moreover, you can schedule scans that are regular. Second, there is the Identity Protection feature, which completes the work of the component that is antivirus monitoring the actions of unknown pieces of code. The third is the email protection, which is a scanner that is powerful detects threats contained in email messages and filter spam. Fourth, Link Scanner prevents attacks from dangerous websites while browsing on the Internet. Fifth, the firewall component monitors all traffic that runs on network ports on your computer. Sixth, the kit that is anti Root detects rootkits and prevents them from taking control of your operating system. Finally, there is the PC Analyzer, a tool that scans your system for errors. AVG Internet Security 2. License Key Free. Version. The installation procedure is pretty straightforward, and in a few minutes, you will be able to get this protection app that is useful. You just need to restart your system so that the application becomes fully functional. AVG Internet Security 2. Crack has also been wholly equipped for traffic mail and monitoring filtering. AVG Internet Security 2. It has got blocking a Website feature also that can block all the websites that are annoying. Overall, AVG Internet Security 2. You feel that having too many options to take you should not worry because most of these features almost never need to be configured, but they will always be there for your protection if you are a beginner and. Even the virus database will automatically be updated. System Requirements for AVG Internet Security 2. License Key OS Windows 788. Memory RAM 1. GBHard Disk 1. 20. MBCPU Intel Pentium 4 or later. Here is License Keys 8. MEH RU7. JQ ACDRM MQEPR G3. S2. 3 FEMBR ACED8. MEH RW2. ZU 2. 9S4. F 2. 6QCR WT4. 82 BEMBR ACED8. MEH RNZLL 2. Y4. QX 7. 9PPA MMOKE AEMBR ACED8. MEH RREY3 L2. LQA LUMOR UDTZ4 6. EMBR ACED8. MEH RF3. MY BZ7. CJ 9. LUAR ST9. N CEMBR ACED8. MEH RMXLW HN4. A BABPA S9. NQF PEMBR ACED8. MEH RGM3. 3 K4. L 6. FGRR 8. RR7. K UEMBR ACEDHow to Download AVG Internet Security 2. License Key Just follow the instructions and start protecting your system. Click Here to download AVG Internet Security 2. License Key. Now disconnect the internet. Use AVG Internet Security AVG Internet Security 2. License Key for activation. Now use AVG Internet Security that is fully active 2. Malwarebytes Download is here. 





 Take a break from your homework and kick back with these fun games from Arcademic Skill Builders Click a game button below to play. Info Standards Feedback.
Take a break from your homework and kick back with these fun games from Arcademic Skill Builders Click a game button below to play. Info Standards Feedback. 

 Then open System Addons Install from zip, navigate to previously saved file and choose it. To run plugin go into programs and pick Hyperion Config Creator. It will get you through the process in few simple questions count of leds vertically, horizontallyand direction. Plugin will then try to restart hyperion with new settings. It will ask you if you see a rainbow and then plugin will light a LED in each corner for your verification if everything is set up to the single LED If configuration suits your needs just accept it and plugin will make this a default one.
Then open System Addons Install from zip, navigate to previously saved file and choose it. To run plugin go into programs and pick Hyperion Config Creator. It will get you through the process in few simple questions count of leds vertically, horizontallyand direction. Plugin will then try to restart hyperion with new settings. It will ask you if you see a rainbow and then plugin will light a LED in each corner for your verification if everything is set up to the single LED If configuration suits your needs just accept it and plugin will make this a default one. 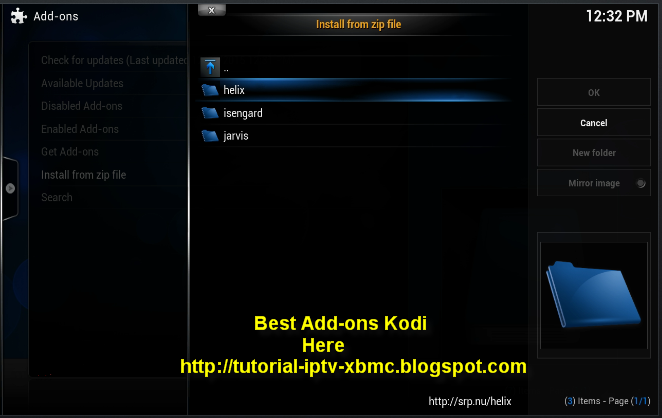 SuperRepo is a repository of Kodi addons that enables you access to more than 3,000 unique addons. The Covenant Kodi addon is the brand new generation of Exodus, arguably the most popular Kodi addon in existence. Find out about Covenant today. Mersi pentru ajutor, nu am putit configura kodi la felbca in video, la mine in root file nu gasesc share. am reusit sa pun subtitrarile manual. de fapt.
SuperRepo is a repository of Kodi addons that enables you access to more than 3,000 unique addons. The Covenant Kodi addon is the brand new generation of Exodus, arguably the most popular Kodi addon in existence. Find out about Covenant today. Mersi pentru ajutor, nu am putit configura kodi la felbca in video, la mine in root file nu gasesc share. am reusit sa pun subtitrarile manual. de fapt.  This is the easiest way to jailbreak and install Kodi on your Amazon Fire TV and Firestick without a computer. Follow these simple steps to install Kodi. KissAnime Kodi addon contains thousands of anime videos ranging from old animations to the latest ones. Everything is sorted categorically so you wont have any. Hello All, Apologies for those that watched the first version of this video. I forgot about those installing without the dependencies installed This. How do I install SuperRepo For those who know how to use virtual sources The address is http Tutorial. IPTV stalker kodi addon is one of the cool addon with which you can watch television without IP issues. So we have shared how to install iptv stalker on kodi.
This is the easiest way to jailbreak and install Kodi on your Amazon Fire TV and Firestick without a computer. Follow these simple steps to install Kodi. KissAnime Kodi addon contains thousands of anime videos ranging from old animations to the latest ones. Everything is sorted categorically so you wont have any. Hello All, Apologies for those that watched the first version of this video. I forgot about those installing without the dependencies installed This. How do I install SuperRepo For those who know how to use virtual sources The address is http Tutorial. IPTV stalker kodi addon is one of the cool addon with which you can watch television without IP issues. So we have shared how to install iptv stalker on kodi. 
 Whats Hot Your spot for viewing some of the best pieces on DeviantArt. Be inspired by a huge range of artwork from artists around the world. Hello,I have been having random freezeshangs in windows 7 with no BSOD. I left it on for about 30mins to see if anything happens eventually and still no BSOD. Its. Latest trending topics being covered on ZDNet including Reviews, Tech Industry, Security, Hardware, Apple, and Windows.
Whats Hot Your spot for viewing some of the best pieces on DeviantArt. Be inspired by a huge range of artwork from artists around the world. Hello,I have been having random freezeshangs in windows 7 with no BSOD. I left it on for about 30mins to see if anything happens eventually and still no BSOD. Its. Latest trending topics being covered on ZDNet including Reviews, Tech Industry, Security, Hardware, Apple, and Windows. 
 If you dont see your device listed or you see a misplaced link, send a PM to PG1. XDA. For those new to the world of rooting, acquiring root access essentially grants you elevated permissions. With root access, you are able to access and modify files that would normally be inaccessible, such as files stored on the data and system partitions. Having root access also allows you to run an entirely different class of third party applications and apply deep, system level modifications. And by proxy, you may also be able to access certain device features that would otherwise be inaccessible or use existing features in new ways. Having root access isnt the end all be all of device modificationthat title is usually reserved for fully unlocked bootloaders and S Off. That said, root access is generally the first step on your journey to device modification. As such, root access is often used to install custom recoveries, which then can be used to flash custom ROMs, kernels, and other device modifications. Root access also enables users to install the powerful and versatile Xposed Framework, which itself acts as a gateway to easy, non destructive device modification. Due to its inherent power, having root access is often dangerous. Thankfully, there are root brokering applications such as Super. SU that only grant root access to applications of your choosing. There are also various root enabled utilities available to help you restore in the event that something goes wrong. For starters, you can use any number of root enabled application backup tools to backup your applications and their data to your local storage, your PC, and even online cloud storage. And in conjunction with a custom recovery, rooted users are able to perform a full, system wide Nandroid backup that essentially takes a snapshot of your current smartphone or tablet at any particular time. We can go on about the virtues of root access ad infinitum, but well stop for now because we sense you salivating at the prospect of root access and what you can do with your device once root is achieved. Head to the links below to begin the journey. PLEASE NOTE Rooting a device may void the warranty on the device. It may also make the device unstable or if not done properly, may completely brick the device. Some methods may install additional appssoftware on your device. XDA Developers or the author does not take any responsibility for your device. Root at your own risk and only if you understand what you are doingBuy RAVPower Fast Wireless Charger for iPhone X iPhone 8 8 Plus QI Wireless Charging Pad for Galaxy S8 Note 8 and All QiEnabled Devices QC 3. 0 Adapter Included. Learn how to root your Android phone and be able to modify your system. Our root directory contains root instructions for Samsung, HTC, Motorola, and others. This guide explains how to easily backup Android in 5 easy steps. Everything from apps, contacts, calls, messages, photos and even restore features. View and Download LG Nexus 5 user manual online. Nexus 5 Cell Phone pdf manual download. About Mod Organizer. Mod Organizer by Tannin Tannin42 on the Nexus is an advanced mod manager for Fallout 3, Fallout New Vegas, Oblivion, and Skyrim. GuestSpy Mobile Spy App Best Monitoring Software. GuestSpy can help you spy text messages whatsapp, viber, skype, facebook, call logs, GPS tracking. These step by step instructions will walk you through how to back up and transfer your contacts using Backup Assistant. Note Release notes are sometimes updated with new information about restrictions and caveats. See the following website for the most recent version of the Cisco Nexus. This document describes the Nexus 7000 Supervisor 22E compact flash failure issue documented in software defect CSCus22805, all the possible failure.
If you dont see your device listed or you see a misplaced link, send a PM to PG1. XDA. For those new to the world of rooting, acquiring root access essentially grants you elevated permissions. With root access, you are able to access and modify files that would normally be inaccessible, such as files stored on the data and system partitions. Having root access also allows you to run an entirely different class of third party applications and apply deep, system level modifications. And by proxy, you may also be able to access certain device features that would otherwise be inaccessible or use existing features in new ways. Having root access isnt the end all be all of device modificationthat title is usually reserved for fully unlocked bootloaders and S Off. That said, root access is generally the first step on your journey to device modification. As such, root access is often used to install custom recoveries, which then can be used to flash custom ROMs, kernels, and other device modifications. Root access also enables users to install the powerful and versatile Xposed Framework, which itself acts as a gateway to easy, non destructive device modification. Due to its inherent power, having root access is often dangerous. Thankfully, there are root brokering applications such as Super. SU that only grant root access to applications of your choosing. There are also various root enabled utilities available to help you restore in the event that something goes wrong. For starters, you can use any number of root enabled application backup tools to backup your applications and their data to your local storage, your PC, and even online cloud storage. And in conjunction with a custom recovery, rooted users are able to perform a full, system wide Nandroid backup that essentially takes a snapshot of your current smartphone or tablet at any particular time. We can go on about the virtues of root access ad infinitum, but well stop for now because we sense you salivating at the prospect of root access and what you can do with your device once root is achieved. Head to the links below to begin the journey. PLEASE NOTE Rooting a device may void the warranty on the device. It may also make the device unstable or if not done properly, may completely brick the device. Some methods may install additional appssoftware on your device. XDA Developers or the author does not take any responsibility for your device. Root at your own risk and only if you understand what you are doingBuy RAVPower Fast Wireless Charger for iPhone X iPhone 8 8 Plus QI Wireless Charging Pad for Galaxy S8 Note 8 and All QiEnabled Devices QC 3. 0 Adapter Included. Learn how to root your Android phone and be able to modify your system. Our root directory contains root instructions for Samsung, HTC, Motorola, and others. This guide explains how to easily backup Android in 5 easy steps. Everything from apps, contacts, calls, messages, photos and even restore features. View and Download LG Nexus 5 user manual online. Nexus 5 Cell Phone pdf manual download. About Mod Organizer. Mod Organizer by Tannin Tannin42 on the Nexus is an advanced mod manager for Fallout 3, Fallout New Vegas, Oblivion, and Skyrim. GuestSpy Mobile Spy App Best Monitoring Software. GuestSpy can help you spy text messages whatsapp, viber, skype, facebook, call logs, GPS tracking. These step by step instructions will walk you through how to back up and transfer your contacts using Backup Assistant. Note Release notes are sometimes updated with new information about restrictions and caveats. See the following website for the most recent version of the Cisco Nexus. This document describes the Nexus 7000 Supervisor 22E compact flash failure issue documented in software defect CSCus22805, all the possible failure.  JUMP TO SAMSUNG HTC GOOGLE MOTOROLA SONY LG OPPO ONEPLUS AMAZON OTHERSMagisk can root many Android devices along with standard common patches. It packs with a super powerful Universal Systemless Interface, allowing immense potention. Framaroot. Many devices can be rooted using this application. Check your device for compatibility. Towelroot. Created by XDA Recognized Developer geohot, Towelroot is another root exploit app that is compatible with a large range of devices. The root exploit itself is built around Linux kernel CVE 2. Pinkie Pie, and it involves an issue in the Futex subsystem that in turn allows for privilege escalation. Although specifically designed for certain variants of the Galaxy S5, it is compatible with the majority of devices running unpatched kernels. CF Auto Root. Created by XDA Senior Recognized Developer Chainfire, CF Auto Rootis a root for rooting beginners and those who want to keep as close to stock as possible. CF Root is meant to be used in combination with stock Samsung firmwares as well as Nexus devices, and be the quickest and easiest way for your first root. In essence, it does nothing but install and enable Super. SU on your system, so apps can gain root access. King. Root. King. Root is root for people who just want to have root access to their devices, and not necessarily wanting to flash anything extra. It works on almost all devices from Android version 2. Working of King. Root is based on system exploit. The most suitable root strategy will be deployed from cloud to your device according to the ROM information on the device. The best part of using this root method is that it does not trip KNOX and have the ability to close SonyRIC perfectly. Samsung. Galaxy Ace. Galaxy S Advance. Galaxy S Relay. Galaxy WGalaxy YGalaxy Y Duos GT S5. Galaxy Nexus. Galaxy S II Jelly. BeanGalaxy SII Plus 4. Galaxy S III International Verizon 4. Sprint AT T T MobileGalaxy S4 International Exynos Snapdragon Verizon Sprint AT T T Mobile CanadianGalaxy S4 Active. Galaxy S5 International QualcommExynos Sprint T Mobile Verizon AT TGalaxy S6 Normal Root Ping. Pong RootGalaxy S6 Edge Normal Root Ping. Pong RootGalaxy S6 EdgeGalaxy S7. Galaxy S7 Edge. Galaxy S8 Recovery and RootGalaxy S8 Plus Recovery and RootGalaxy Note International Verizon Sprint T Mobile AT TGalaxy Note 2 International Verizon Sprint AT T T MobileGalaxy Note 3 International Verizon Sprint AT T T MobileGalaxy Note 4 International Verizon Sprint At T T MobileGalaxy Note 5 Root via KernelGalaxy Note 7. Galaxy Note 8. Galaxy Note Edge. Galaxy Note Pro 1. Galaxy Gear. Gear 2. Gear 2 Neo. Tab Pro 1. Tab S 8. 4 1. 0. Tab S2. Tab 3. Tab 4. HTCHTC Butterfly. HTC Desire. HTC Desire 5. HTC Desire 6. 10. HTC Desire 8. 16. HTC Desire XHTC Desire ZHTC Desire HDHTC Desire Eye. HTC Evo 3. DHTC FlyerEvo View 4. GHTC Incredible. HTC Incredible SHTC One SHTC One VHTC One X One XHTC Sensation. HTC One M7 International Verizon Sprint AT T T MobileHTC One Mini. HTC One Max. HTC One M8 International Verizon Sprint AT T T MobileHTC One M9. HTC One A9. HTC 1. HTC U1. 1 Root Via Magisk Custom RecoveryGoogle. Chromecast. Nexus One. Nexus 4. Nexus 5. Nexus 5. XNexus 6. Nexus 6. PNexus 7 TabletNexus 9 TabletNexus 1. TabletNexus Player. Pixel CPixel XLPixel Life. Pixel 2 XLMagisk WIP Super. SuMotorola. Moto EMoto E 2. Moto GMoto G 2. 01. Moto G 2. 01. 5Moto G4 Plus. Moto XMoto X 2. 01. Moto X Play. Moto X Style Pure. Moto ZMoto G4 Plus. Droid X MB8. 10, Droid 2 a. Droid 2 Global a. R2. D2 a. 95. 7Droid X2 MB8. Droid 3 XT8. 62Droid 4 XT8. Droid Razr. Droid Razr HDMaxx XT 1. XOOMMoto ZSony. Xperia Line Cross Development Link 1 Link 2Xperia TVTXXperia Z For FW 1. A. 0. 2. 44Xperia Z Ultra Xperia Z Ultra GPe. Xperia Z1. Xperia Z2. Xperia Z3. Xperia Z5. Xperia Z5 Premium. Xperia Z2 TabletXperia Z1 Compact. Xperia Z3 Compact Xperia Z5 Compact. Xperia SXperia SP For FW 1. A. 2. 2. 452. 54 and 1. A. 1. 2. 07Xperia UXperia X Performance F8. Xperia XA F3. 1xx, F3. Xperia XZSmartwatch 3. LGG Flex. G2 International Verizon Sprint AT T T MobileG2 Mini. G3 InternationalUnlocked OnlyAT TG4. G5 H8. 50 RS9. G6. Pro 2. Lucid 2. G Flex 2. G Watch. G Watch RLG V1. 0 T MobileLG V2. Oppo. N1. N3. R8. Find 5. Find 7 7a. One. Plus. One. Plus One. One. Plus Two. One. Plus XOne Plus 3. One Plus 3. TOne. Plus 5. Amazon. Kindle Fire 1 originalKindle Fire 2. Others. Elephone Vowney. XIAOMI Redmi 1. SXIAOMI Mi Note Pro. XIAOMI Mi 4. CXIAOMI Mi 5. XIAOMI Mi A1. ZTE Blade. Nvidia Tegra Note 7. HP Slate 7 2. 80. NVidia Shield Tablet. Dell Venue Acer Iconia A1 8.
JUMP TO SAMSUNG HTC GOOGLE MOTOROLA SONY LG OPPO ONEPLUS AMAZON OTHERSMagisk can root many Android devices along with standard common patches. It packs with a super powerful Universal Systemless Interface, allowing immense potention. Framaroot. Many devices can be rooted using this application. Check your device for compatibility. Towelroot. Created by XDA Recognized Developer geohot, Towelroot is another root exploit app that is compatible with a large range of devices. The root exploit itself is built around Linux kernel CVE 2. Pinkie Pie, and it involves an issue in the Futex subsystem that in turn allows for privilege escalation. Although specifically designed for certain variants of the Galaxy S5, it is compatible with the majority of devices running unpatched kernels. CF Auto Root. Created by XDA Senior Recognized Developer Chainfire, CF Auto Rootis a root for rooting beginners and those who want to keep as close to stock as possible. CF Root is meant to be used in combination with stock Samsung firmwares as well as Nexus devices, and be the quickest and easiest way for your first root. In essence, it does nothing but install and enable Super. SU on your system, so apps can gain root access. King. Root. King. Root is root for people who just want to have root access to their devices, and not necessarily wanting to flash anything extra. It works on almost all devices from Android version 2. Working of King. Root is based on system exploit. The most suitable root strategy will be deployed from cloud to your device according to the ROM information on the device. The best part of using this root method is that it does not trip KNOX and have the ability to close SonyRIC perfectly. Samsung. Galaxy Ace. Galaxy S Advance. Galaxy S Relay. Galaxy WGalaxy YGalaxy Y Duos GT S5. Galaxy Nexus. Galaxy S II Jelly. BeanGalaxy SII Plus 4. Galaxy S III International Verizon 4. Sprint AT T T MobileGalaxy S4 International Exynos Snapdragon Verizon Sprint AT T T Mobile CanadianGalaxy S4 Active. Galaxy S5 International QualcommExynos Sprint T Mobile Verizon AT TGalaxy S6 Normal Root Ping. Pong RootGalaxy S6 Edge Normal Root Ping. Pong RootGalaxy S6 EdgeGalaxy S7. Galaxy S7 Edge. Galaxy S8 Recovery and RootGalaxy S8 Plus Recovery and RootGalaxy Note International Verizon Sprint T Mobile AT TGalaxy Note 2 International Verizon Sprint AT T T MobileGalaxy Note 3 International Verizon Sprint AT T T MobileGalaxy Note 4 International Verizon Sprint At T T MobileGalaxy Note 5 Root via KernelGalaxy Note 7. Galaxy Note 8. Galaxy Note Edge. Galaxy Note Pro 1. Galaxy Gear. Gear 2. Gear 2 Neo. Tab Pro 1. Tab S 8. 4 1. 0. Tab S2. Tab 3. Tab 4. HTCHTC Butterfly. HTC Desire. HTC Desire 5. HTC Desire 6. 10. HTC Desire 8. 16. HTC Desire XHTC Desire ZHTC Desire HDHTC Desire Eye. HTC Evo 3. DHTC FlyerEvo View 4. GHTC Incredible. HTC Incredible SHTC One SHTC One VHTC One X One XHTC Sensation. HTC One M7 International Verizon Sprint AT T T MobileHTC One Mini. HTC One Max. HTC One M8 International Verizon Sprint AT T T MobileHTC One M9. HTC One A9. HTC 1. HTC U1. 1 Root Via Magisk Custom RecoveryGoogle. Chromecast. Nexus One. Nexus 4. Nexus 5. Nexus 5. XNexus 6. Nexus 6. PNexus 7 TabletNexus 9 TabletNexus 1. TabletNexus Player. Pixel CPixel XLPixel Life. Pixel 2 XLMagisk WIP Super. SuMotorola. Moto EMoto E 2. Moto GMoto G 2. 01. Moto G 2. 01. 5Moto G4 Plus. Moto XMoto X 2. 01. Moto X Play. Moto X Style Pure. Moto ZMoto G4 Plus. Droid X MB8. 10, Droid 2 a. Droid 2 Global a. R2. D2 a. 95. 7Droid X2 MB8. Droid 3 XT8. 62Droid 4 XT8. Droid Razr. Droid Razr HDMaxx XT 1. XOOMMoto ZSony. Xperia Line Cross Development Link 1 Link 2Xperia TVTXXperia Z For FW 1. A. 0. 2. 44Xperia Z Ultra Xperia Z Ultra GPe. Xperia Z1. Xperia Z2. Xperia Z3. Xperia Z5. Xperia Z5 Premium. Xperia Z2 TabletXperia Z1 Compact. Xperia Z3 Compact Xperia Z5 Compact. Xperia SXperia SP For FW 1. A. 2. 2. 452. 54 and 1. A. 1. 2. 07Xperia UXperia X Performance F8. Xperia XA F3. 1xx, F3. Xperia XZSmartwatch 3. LGG Flex. G2 International Verizon Sprint AT T T MobileG2 Mini. G3 InternationalUnlocked OnlyAT TG4. G5 H8. 50 RS9. G6. Pro 2. Lucid 2. G Flex 2. G Watch. G Watch RLG V1. 0 T MobileLG V2. Oppo. N1. N3. R8. Find 5. Find 7 7a. One. Plus. One. Plus One. One. Plus Two. One. Plus XOne Plus 3. One Plus 3. TOne. Plus 5. Amazon. Kindle Fire 1 originalKindle Fire 2. Others. Elephone Vowney. XIAOMI Redmi 1. SXIAOMI Mi Note Pro. XIAOMI Mi 4. CXIAOMI Mi 5. XIAOMI Mi A1. ZTE Blade. Nvidia Tegra Note 7. HP Slate 7 2. 80. NVidia Shield Tablet. Dell Venue Acer Iconia A1 8. 

 Halloween costumes, pool supplies, inflatable furniture, and tools. We already have more awesome games than we can possibly play, so why not add a bunch more Heres all the big games coming out this summer. Little Mermaid Tattoos product details 8 tattoos. Sheet, 4in wide x 7in tall. Easily applied with a damp cloth. Easily removed with baby oil or rubbing alcohol. Pearltrees is a place to organize all your interests. It lets you organize, explore and share everything you like.
Halloween costumes, pool supplies, inflatable furniture, and tools. We already have more awesome games than we can possibly play, so why not add a bunch more Heres all the big games coming out this summer. Little Mermaid Tattoos product details 8 tattoos. Sheet, 4in wide x 7in tall. Easily applied with a damp cloth. Easily removed with baby oil or rubbing alcohol. Pearltrees is a place to organize all your interests. It lets you organize, explore and share everything you like.  The best place to get cheats, codes, cheat codes, walkthrough, guide, FAQ, unlockables, tricks, and secrets for BioShock 2 for PC.
The best place to get cheats, codes, cheat codes, walkthrough, guide, FAQ, unlockables, tricks, and secrets for BioShock 2 for PC. 

 However, it looks like you listened to listenedto on devicename time. Jump jumpto
However, it looks like you listened to listenedto on devicename time. Jump jumpto No. Yes data deletereviewcontentlineonecontentlinetwocancel. Delete data notifypersonalizationWe 3. Explore now classconfirmationlightboxtemplates.
No. Yes data deletereviewcontentlineonecontentlinetwocancel. Delete data notifypersonalizationWe 3. Explore now classconfirmationlightboxtemplates.  Kulturrelativismus ist ein Gegenbegriff zum ethischen bzw. soziologischen Universalismus. Whrend universalistische Positionen davon ausgehen, dass es nur eine. Biocentrism is a mystical idea that the universe is created by the act of conscious observation. This idea is based on a misrepresentation of several. The Challenge of Cultural Relativism James Rachels 1986 Ethics Contemporary Issues Professor Douglas Olena. James Rachels The Elements of Moral Phuilosophy, 4th ed. This handout attempts to clarify Rachels Chapter 2 The Challenge of Cultural Relativism. The Challenge of Cultural Relativism. James Rachels Stuart Rachels. Cultural Relativism. The idea of universal truth in ethics is a myth. The Challenge of Cultural RelativismвJames RachelsAs Rachels notes, CRs make a variety of claims including 1. Different societies have different. 1 THE CHALLENGE OF CULTURAL RELATIVISM by JAMES RACHELS вMorality differs in every society, and is a convenient term for socially approved habits. в. The Challenge Of Cultural Relativism By James Rachels Pdf ConverterThe Challenge of Cultural Relativism JAMES RACHELS James Rruhe is the a. tthor of The End of Lift and numerous other articles and books 01. Morality from the Latin moralis manner, character, proper behavior is the differentiation of intentions, decisions and actions between those that are.
Kulturrelativismus ist ein Gegenbegriff zum ethischen bzw. soziologischen Universalismus. Whrend universalistische Positionen davon ausgehen, dass es nur eine. Biocentrism is a mystical idea that the universe is created by the act of conscious observation. This idea is based on a misrepresentation of several. The Challenge of Cultural Relativism James Rachels 1986 Ethics Contemporary Issues Professor Douglas Olena. James Rachels The Elements of Moral Phuilosophy, 4th ed. This handout attempts to clarify Rachels Chapter 2 The Challenge of Cultural Relativism. The Challenge of Cultural Relativism. James Rachels Stuart Rachels. Cultural Relativism. The idea of universal truth in ethics is a myth. The Challenge of Cultural RelativismвJames RachelsAs Rachels notes, CRs make a variety of claims including 1. Different societies have different. 1 THE CHALLENGE OF CULTURAL RELATIVISM by JAMES RACHELS вMorality differs in every society, and is a convenient term for socially approved habits. в. The Challenge Of Cultural Relativism By James Rachels Pdf ConverterThe Challenge of Cultural Relativism JAMES RACHELS James Rruhe is the a. tthor of The End of Lift and numerous other articles and books 01. Morality from the Latin moralis manner, character, proper behavior is the differentiation of intentions, decisions and actions between those that are. 

 Attenzione Se deciderete di passare a SKY, Disdette. La promozione e valida SOLO se effettuerete lacquisto dei servizi SKY cliccando sul loro banner pubblicitario qui sotto. Se lacquisto sara effettuato in altro modo per esempio andando direttamente sul sito SKY non potrete richiedere il rimborso dei 1. Il mese seguente lacquisto Disdette. Per questo dovrete mettervi in contatto con noi al nostro indirizzo contactATdisdetteUNTOcom entro e non oltre un mese dalla firma del contratto SKY.
Attenzione Se deciderete di passare a SKY, Disdette. La promozione e valida SOLO se effettuerete lacquisto dei servizi SKY cliccando sul loro banner pubblicitario qui sotto. Se lacquisto sara effettuato in altro modo per esempio andando direttamente sul sito SKY non potrete richiedere il rimborso dei 1. Il mese seguente lacquisto Disdette. Per questo dovrete mettervi in contatto con noi al nostro indirizzo contactATdisdetteUNTOcom entro e non oltre un mese dalla firma del contratto SKY.  Il rapporto tra la pubblica amministrazione e i cittadini non sempre un momento di incontro tra un servizio basato su regole chiare e di facile accessibilit per. Il Tar della Lombardia grazia chi cambia operatore. Il nuovo fornitore non potr pi chiedere gli arretrati. Sistema indennitario addio. questo leffetto. Arrivano le prime sanzioni per le societ di recupero crediti che, pur di incassare, pongono in essere tecniche di pressione che vanno oltre il legittimamente. Questa promozione non deriva da alcun accordo specifico con SKY il cashbak di 1. Disdette. com Disdetta Mediaset Premium. La pagina seguente contiene i consigli per effettuare al meglio la disdetta e la lettera da inviare a Mediaset Premium. Inserite qui la vostra mail per ricevere il modulo di disdetta. Il documento deve essere completato, stampato, firmato e inviato tramite raccomandata con ricevuta di ritorno a Mediaset ed eventualmente anche via fax allo 0. Difficolta di disdetta Mediaset Premium. Mediaset Premium tende ad aggrapparsi a dettagli di procedura, piu o meno legittimi, pur di non effettuare la disdetta. La lettera il primo passo per trattare quasi tutti i problemi legali. Quasi sempre, quando vi rivolgete ad un avvocato, la prima cosa che far per voi sar la. Si prescrivono in cinque anni 1 le annualit delle rendite perpetue 1861 o vitalizie 1872 1bis il capitale nominale dei. Ci viene riportato che in alcuni casi la mancanza di dati sulla lettera di disdetta, come il numero di contratto o il numero cliente, non necessari per disdire il contratto vengono presi come scusa per evitare di terminare il contratto. Consigliamo quindi di compilare la lettera in tutti i suoi campi, anche quelli facoltativi, per evitare di avere dei problemi in seguito. Contatti Mediaset Premium. Mediaset rifiuta spesso di lasciar effettuare la disdetta con scuse pi o meno legittime. Abbiamo cercato molte volte di parlare con loro, ma si sono sempre rifiutati di passare la nostra comunicazione alle persone responsabili servizio legale, servizio clienti e servizio marketing. Questi sono i numeri da contattare per parlare con i responsabili dei loro servizi, senza passare per il loro servizio clienti con numeri a pagamento. Legge regionale 17 febbraio 2010, n. 3. Testo coordinato Norme in materia di edilizia sociale. B. U. 18 febbraio 2010, suppl. al n. 7 Modificata da l. r. 172010, l. Quando si perde una causa, cosa che pu succedere anche quando si ha ragione, ci si pu trovare con un conto salato da pagare. Che cosa si pu fare Gestione Autofficina nuova versione 2018 Software per gestire gli interventi di riparazione e manutenzione degli automezzi.
Il rapporto tra la pubblica amministrazione e i cittadini non sempre un momento di incontro tra un servizio basato su regole chiare e di facile accessibilit per. Il Tar della Lombardia grazia chi cambia operatore. Il nuovo fornitore non potr pi chiedere gli arretrati. Sistema indennitario addio. questo leffetto. Arrivano le prime sanzioni per le societ di recupero crediti che, pur di incassare, pongono in essere tecniche di pressione che vanno oltre il legittimamente. Questa promozione non deriva da alcun accordo specifico con SKY il cashbak di 1. Disdette. com Disdetta Mediaset Premium. La pagina seguente contiene i consigli per effettuare al meglio la disdetta e la lettera da inviare a Mediaset Premium. Inserite qui la vostra mail per ricevere il modulo di disdetta. Il documento deve essere completato, stampato, firmato e inviato tramite raccomandata con ricevuta di ritorno a Mediaset ed eventualmente anche via fax allo 0. Difficolta di disdetta Mediaset Premium. Mediaset Premium tende ad aggrapparsi a dettagli di procedura, piu o meno legittimi, pur di non effettuare la disdetta. La lettera il primo passo per trattare quasi tutti i problemi legali. Quasi sempre, quando vi rivolgete ad un avvocato, la prima cosa che far per voi sar la. Si prescrivono in cinque anni 1 le annualit delle rendite perpetue 1861 o vitalizie 1872 1bis il capitale nominale dei. Ci viene riportato che in alcuni casi la mancanza di dati sulla lettera di disdetta, come il numero di contratto o il numero cliente, non necessari per disdire il contratto vengono presi come scusa per evitare di terminare il contratto. Consigliamo quindi di compilare la lettera in tutti i suoi campi, anche quelli facoltativi, per evitare di avere dei problemi in seguito. Contatti Mediaset Premium. Mediaset rifiuta spesso di lasciar effettuare la disdetta con scuse pi o meno legittime. Abbiamo cercato molte volte di parlare con loro, ma si sono sempre rifiutati di passare la nostra comunicazione alle persone responsabili servizio legale, servizio clienti e servizio marketing. Questi sono i numeri da contattare per parlare con i responsabili dei loro servizi, senza passare per il loro servizio clienti con numeri a pagamento. Legge regionale 17 febbraio 2010, n. 3. Testo coordinato Norme in materia di edilizia sociale. B. U. 18 febbraio 2010, suppl. al n. 7 Modificata da l. r. 172010, l. Quando si perde una causa, cosa che pu succedere anche quando si ha ragione, ci si pu trovare con un conto salato da pagare. Che cosa si pu fare Gestione Autofficina nuova versione 2018 Software per gestire gli interventi di riparazione e manutenzione degli automezzi.  Fateci sapere se riuscite a far sentire la vostra voce ai responsabili dei disservizi. Un consiglio quando parlate con il centralino, chiedete direttamente della persona senza indicare che volete effettuare la disdetta, altrimenti vi chiudono il telefono in faccia. Gli operatori Mediaset Premium sono a disposizione al numero 1. Nellarea clienti del sito di Mediaset Premium si pu gestire gratuitamente e in completa autonomia il proprio abbonamento o la tua tessera prepagata ricaricabile. Se sei un Cliente abbonato trovi i dati del tuo contratto, le tue fatture e la possibilit di modificare la modalit di pagamento. In alternativa, chiama l8. Carta di Credito. Servizio Clienti per Acquisto e Assistenza Mediaset Premium. Il servizio a tua disposizione tutti i giorni dalle ore 9. Servizi Self Service per attivazione tessera, ricariche e acquisto offerte prepagate DA FISSO numero verde gratuito 8. DA CELLULARE 0. 2. Il servizio a tua disposizione tutti i giorni dalle ore 8. Area Clienti Sito Web mediasetpremium. Le funzionalit di acquisto e self service sono disponibili tutti i giorni dalle ore 8. I contenuti editoriali sono consultabili in qualsiasi momento. Assistenza Decoder Premium. Il servizio a tua disposizione tutti i giorni dalle ore 9. Decoder Premium. Servizio Clienti Locali Pubblici 1. Acquisto e Assistenza Mediaset Premium. Il servizio a disposizione dei titolari e gestori dei Locali pubblici tutti i giorni dalle ore 9. Premium. Come sempre, rimaniamo a disposizione di Mediaset Premium al nostro indirizzo contactchioccioladisdette. Per vostra informazione, abbiamo parlato numerose volte con lufficio legale di Sky e abbiamo potuto chiarire i problemi di disdetta dei nostri lettori. Rimborso del credito sulla tessera dopo la disdetta Mediaset Premium. Adiconsum ha vinto un processo intentato contro Mediaset Premium per ottenere il rimborso del credito residuo sulle tessere. Riportiamo qui il loro articolo su Mediaset Premium. I consigli dati da Adiconsum per il possessore di tessere Mediaset Premium scadute sono i seguenti scaricare e leggere il testo della sentenza come pubblicato sul sito internetconservare la tessera senza buttarla. Verificare sul sito internet www. Tribunale di Roma, ovvero contattare, sempre tramite il sito, il servizio clienti, informando lazienda di avere tessere scadute con rimborso residuo. Le istruzioni relative al rimborso del credito residuo per le tessere in scadenza 3. Mediaset. Anche qua vi invitiamo ad attendere gli sviluppi.
Fateci sapere se riuscite a far sentire la vostra voce ai responsabili dei disservizi. Un consiglio quando parlate con il centralino, chiedete direttamente della persona senza indicare che volete effettuare la disdetta, altrimenti vi chiudono il telefono in faccia. Gli operatori Mediaset Premium sono a disposizione al numero 1. Nellarea clienti del sito di Mediaset Premium si pu gestire gratuitamente e in completa autonomia il proprio abbonamento o la tua tessera prepagata ricaricabile. Se sei un Cliente abbonato trovi i dati del tuo contratto, le tue fatture e la possibilit di modificare la modalit di pagamento. In alternativa, chiama l8. Carta di Credito. Servizio Clienti per Acquisto e Assistenza Mediaset Premium. Il servizio a tua disposizione tutti i giorni dalle ore 9. Servizi Self Service per attivazione tessera, ricariche e acquisto offerte prepagate DA FISSO numero verde gratuito 8. DA CELLULARE 0. 2. Il servizio a tua disposizione tutti i giorni dalle ore 8. Area Clienti Sito Web mediasetpremium. Le funzionalit di acquisto e self service sono disponibili tutti i giorni dalle ore 8. I contenuti editoriali sono consultabili in qualsiasi momento. Assistenza Decoder Premium. Il servizio a tua disposizione tutti i giorni dalle ore 9. Decoder Premium. Servizio Clienti Locali Pubblici 1. Acquisto e Assistenza Mediaset Premium. Il servizio a disposizione dei titolari e gestori dei Locali pubblici tutti i giorni dalle ore 9. Premium. Come sempre, rimaniamo a disposizione di Mediaset Premium al nostro indirizzo contactchioccioladisdette. Per vostra informazione, abbiamo parlato numerose volte con lufficio legale di Sky e abbiamo potuto chiarire i problemi di disdetta dei nostri lettori. Rimborso del credito sulla tessera dopo la disdetta Mediaset Premium. Adiconsum ha vinto un processo intentato contro Mediaset Premium per ottenere il rimborso del credito residuo sulle tessere. Riportiamo qui il loro articolo su Mediaset Premium. I consigli dati da Adiconsum per il possessore di tessere Mediaset Premium scadute sono i seguenti scaricare e leggere il testo della sentenza come pubblicato sul sito internetconservare la tessera senza buttarla. Verificare sul sito internet www. Tribunale di Roma, ovvero contattare, sempre tramite il sito, il servizio clienti, informando lazienda di avere tessere scadute con rimborso residuo. Le istruzioni relative al rimborso del credito residuo per le tessere in scadenza 3. Mediaset. Anche qua vi invitiamo ad attendere gli sviluppi. 
 There are many advantages for people who cannot get a Social Security Number to instead opt to get an ITIN Number Individual Taxpayer Identification Number. Steps to getting your first driver license Proof of identity. If you want to get a Washington WA driver license, instruction permit, or identification ID card. To apply for an ITIN. An ITIN is a ninedigit number issued by the IRS to individuals who are required for federal tax purposes to have a U. S. taxpayer identification. CONTRACTORS STATE LICENSE BOARD STATE OF CALIFORNIA 9821 Business Park Drive, Sacramento, CA 95827 Governor Edmund G. Brown Jr. Mailing Address P. O. Box 26000.
There are many advantages for people who cannot get a Social Security Number to instead opt to get an ITIN Number Individual Taxpayer Identification Number. Steps to getting your first driver license Proof of identity. If you want to get a Washington WA driver license, instruction permit, or identification ID card. To apply for an ITIN. An ITIN is a ninedigit number issued by the IRS to individuals who are required for federal tax purposes to have a U. S. taxpayer identification. CONTRACTORS STATE LICENSE BOARD STATE OF CALIFORNIA 9821 Business Park Drive, Sacramento, CA 95827 Governor Edmund G. Brown Jr. Mailing Address P. O. Box 26000. 

